As we navigate the digital landscape, we often rely on encryption algorithms to protect our personal information, financial transactions, and confidential communications. One such algorithm that plays a crucial role in securing our digital lives is AES encryption.
In an increasingly interconnected world where digital information flows freely, ensuring the privacy and security of sensitive data has become paramount. In this article, we will explore the inner workings of AES encryption, examining each transformation in detail and understanding how they contribute to the algorithm’s strength.
- What is AES Encryption?
- How AES Encryption Works
- Examples of AES Encryption Usage
- Advantages and Disadvantages of AES Encryption
- Security Issues Associated With AES Encryption
- Why Was AES Developed and Introduced?
- Is AES Encryption Secure in the Age of AI?
- Final Thoughts: AES Encryption Keeps Your Data Safe
- AES Encryption Frequently Asked Questions
What is AES Encryption?
AES encryption is a type of encryption that uses a symmetric key. That means that the same key (like a password) is used to both lock (encrypt) and unlock (decrypt) data. It can use different key lengths: 128, 192, and 256 bits. The longer the key, the more secure it is.
Encryption is like a secret code. It turns your data, anything from a message to a credit card number, into a code others can’t read. AES has become the go-to standard worldwide because it’s very secure and works efficiently.
How AES Encryption Works
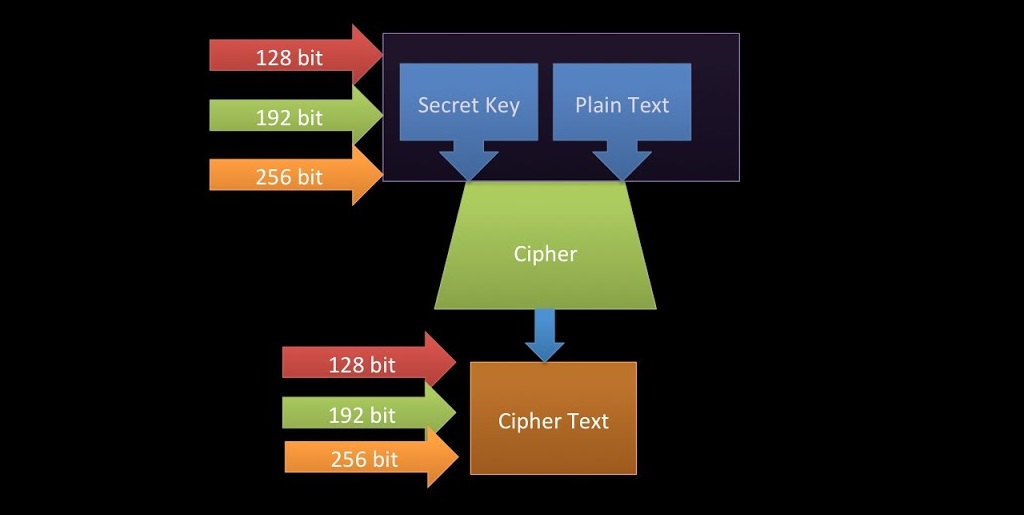
AES encryption turns regular data (plaintext) into encoded data (ciphertext) through a series of steps. These are divided into two parts; Encryption and Decryption. Let’s look at the process in simpler terms:
The AES Encryption Process
This process starts with the preparation of the data and keys. The plaintext data is divided into blocks and arranged in a 4×4 grid. Simultaneously, the encryption key is expanded to create a series of “Round Keys.” Different stages of the process will require these keys.
The data then goes through a set of transformations for each round. The number of rounds depends on the key length:
- 10 rounds for a 128-bit key.
- 12 for 192 bits.
- 4 for 256 bits.
Each round includes:
- SubBytes: Replace each byte (group of 8 bits) with another from a unique table.
- ShiftRows: Shift the bytes around so they’re not in the same place as before.
- MixColumns: Mix the bytes up even more. This step is skipped in the final round.
- AddRoundKey: Combine the transformed data with one of the Round Keys.
The final round is similar but skips the “MixColumns” step. The output is the ciphertext, or encoded data, which can be stored securely.
The AES Decryption Process
Decryption takes the ciphertext and turns it back into the original plaintext. It uses the same round keys and goes through steps like encryption but in reverse.
- Inverse ShiftRows: Shift the bytes back to their original places.
- Inverse SubBytes: Replace each byte with the original one from the unique table.
- AddRoundKey: Combine the transformed data with one of the Round Keys.
- Inverse MixColumns: Unmix the bytes. This is done in all rounds except the final one.
After the correct number of rounds, you get the original data back.
Also Read: Understanding Data Encryption
Examples of AES Encryption Usage
AES encryption is used in numerous scenarios, both in personal and professional settings. Here are some examples of where AES encryption plays a crucial role:
- Secure Website Connections – When you connect to a secure website, your communication with the site is encrypted, often using AES, to protect sensitive data.
- WiFi Security – AES is often used in WiFi security protocols like WPA2 and WPA3. AES helps ensure that the data transmitted between your device and the WiFi router is safe.
- Virtual Private Networks (VPNs) – VPNs use encryption to create a secure tunnel of communication over the internet. AES encryption offers an excellent balance of speed and security.
- Cloud Storage Services – Services like Google Drive, Dropbox, and OneDrive use AES encryption to secure your data when stored on their servers.
- Email Encryption – Secure email providers use AES to encrypt emails in transit and at rest. This helps ensure that only the sender and the receiver can read the contents of the email.
- Mobile Payments – When you use your phone to make a payment, AES encryption is often used to secure the transmission of your payment information, protecting it from potential interceptors.
- Secure Instant Messaging Apps – Messaging apps like WhatsApp and Signal use AES encryption (as part of the Signal Protocol) to ensure that messages exchanged remain confidential.
Advantages and Disadvantages of AES Encryption
As with any technology, AES encryption has its pros and cons. Understanding these will give you a more comprehensive view of its role in digital security.
While AES has its challenges, its benefits significantly outweigh the drawbacks for most users. The robust security, broad acceptance, versatility, efficiency, and compliance support make AES indispensable for protecting digital data.
Advantages of AES Encryption
- Robust Security: AES offers a high level of security. Its 128, 192, and 256-bit key sizes make it extremely difficult to crack. It’s currently considered secure against all known practical attacks when used correctly.
- Widely Accepted Standard: AES is an internationally recognized standard. The U.S. government uses it for encrypting classified information and by businesses and individuals worldwide. This widespread acceptance boosts confidence in its security and reliability.
- Versatility: AES encryption is versatile, applicable across various platforms and for numerous purposes, from encrypting emails to securing cloud storage.
- Efficiency: AES operates efficiently, even on hardware with limited resources. It’s built to run well on various devices, making it suitable for large-scale organizations and individual users.
- Supports Compliance: AES encryption keeps compliance with various privacy regulations. Using it can help businesses meet the standards set by laws such as the General Data Protection Regulation (GDPR) or the California Consumer Privacy Act (CCPA).
Disadvantages of AES Encryption
- Key Management: Like all symmetric encryption algorithms, secure key management can be challenging with AES. Safely distributing these keys, particularly over the internet, can be complex.
- Single Point of Failure: The encrypted data can’t be recovered if the encryption key is lost. Conversely, if the key is stolen, the thief could decrypt any data encrypted with that key. This single point of failure requires secure key storage and management.
- Does Not Protect Data Integrity: While AES provides confidentiality, it does not inherently protect against tampering. Data integrity requires working with other cryptographic protocols, such as in AES-GCM mode.
- Resource Usage: While generally efficient, AES encryption can still be resource-intensive, particularly with larger key sizes. This could slow down systems or use more power when large volumes of data need to be encrypted simultaneously.
Security Issues Associated With AES Encryption
It’s essential to understand that no security solution is 100% foolproof. AES Encryption is the same, and there are some potential security issues of which to be aware.
Side-Channel Attacks
While AES itself is secure, its implementation can sometimes be exploited. Side-channel attacks are one such example. These attacks rely on information gained from the physical system that AES is implemented on, such as timing information and power consumption.
For example, a timing attack involves analyzing how long it takes for a system to encrypt different data inputs to deduce the encryption key. To mitigate side-channel attacks, care must be taken in AES’s hardware and software implementation not to leak such information.
Fault Injection Attacks
The fault injection attack is another form of attack on the implementation rather than the algorithm. This attack involves manipulating the physical system running the AES to induce errors or “faults” in the encryption process.
These faults can sometimes be exploited to reveal the encryption key. Protection against fault injection attacks usually involves adding layers of error-checking and fault tolerance in the hardware and software.
Brute Force Attacks
In theory, AES could be susceptible to a brute force attack, where an attacker tries every possible key until they find the one that decrypts the data. However, the number of possible keys is astronomically large with the key sizes that AES uses (128, 192, and 256 bits).
With current technology and for the foreseeable future, a brute force attack on AES would take an impractical amount of time, making this type of attack largely theoretical.
Why Was AES Developed and Introduced?
AES encryption arose from needing a more robust and efficient encryption standard to replace the aging Data Encryption Standard (DES). DES was a symmetric-key algorithm, meaning the same key was used to encrypt and decrypt the data.
However, DES had a significant flaw: its key length. With a 56-bit key size, DES provided adequate protection during the 1970s and ’80s. But with the advancement of computational power, it became increasingly vulnerable to brute-force attacks.
Recognizing the need for a more secure encryption standard, the National Institute of Standards and Technology (NIST) announced an open competition in 1997 to develop a new encryption algorithm that was to be known as the Advanced Encryption Standard.
The winner, announced in 2001, was a cipher known as Rijndael, created by Belgian cryptographers Vincent Rijmen and Joan Daemen. The Rijndael algorithm was selected for its strong security, speed, simplicity, and ability to handle various block and key sizes. It became the new Advanced Encryption Standard.
Is AES Encryption Secure in the Age of AI?
The evolution of technology, including AI and quantum computing, could pose threats to AES in the future. Quantum computers, in particular, are theorized to be capable of breaking many current encryption algorithms.
Thanks to OpenAI and ChatGPT, AI is a hot topic, but it also has its limitations. It can only express what’s in its training data set and can be maddeningly literal. They are also unpredictable and nondeterministic due to their use of randomness.
Despite significant advancements, AES’s robust mathematical structure remains secure in the context of AI evolution. AI’s strength in pattern recognition doesn’t help with AES, as the encryption process leaves no exploitable patterns or weaknesses.
For now, AES Encryption remains relatively safe.
Final Thoughts: AES Encryption Keeps Your Data Safe
AES Encryption is crucial in safeguarding sensitive data across countless applications, from securing internet connections and cloud storage to protecting mobile payments and private communications.
As we move forward, it’s crucial to understand these encryption methods and ensure their proper implementation and management, maintaining the integrity and confidentiality of our data in an increasingly digital world.
AES Encryption Frequently Asked Questions
Also Read;
The post What is AES Encryption and How Does It Work? appeared first on HideMyTraffic.




