Conti Ransomware has been one of the most infamous strains of ransomware in recent years. The malware itself is expertly written and is able to encrypt data and spread to adjacent systems with speed previously unseen in the ransomware community. It was first observed in 2020, and is lead by a Russian-based cybercrime group simply known as the Conti Ransomware gang. Attacks by Conti have been on a global scale. In May 2022, the US government offered a reward of up to $10 million for information on the Conti ransomware gang.
The Conti Ransomware gang partake in what is known as double extortion. A recent practice in the cybercrime underworld, it is also known as pay-now-or-get-breached. In this strategy, the attacks will first exfiltrate large quantities of private information, and then encrypt the files. Once this is complete, the hackers will threaten to leak the data publicly (or sell it on the darkweb). Unless they are paid a ransom, which is usually in the millions.
After two years of global attacks, the Conti Ransomware gang seemingly shut down last month. Moreover, taking key pieces of its infrastructure offline. The decommissioning took place just weeks have a massive attack on the country of Costa Rica. The attack caused the country to declare a state of emergency.
The shutdown of a ransomware operation is an odd thing. It is not uncommon for the operation to simply rebrand. Othertimes they may just resurface months later. The organization may also splinter off into several smaller gangs. Still, these operations do occasionally shut-down permanently. This remains to be seen for the Conti Ransomware Gang, who now exist as Schrödinger’s Cybercrime Gang, so to speak.
A huge blow to Conti was self-inflicted. Following the invasion of Ukraine, the gang publicly aligned itself with the Russian government. Not only did this move draw ire from the hacking community, who are notoriously anarchistic. The gang has upset some of the wrong people – including one who may have been an ex-member.
Shortly after the Russia announcement, a Ukrainian hacker sent logs of internal Conti conversations to many western publications and cybersecurity researchers around the globe. These logs, compromising of many GB’s of data, shed a light on names, wallet address, online handles, and more of active Conti members. These details can provide law enforcement an edge in perusing Conti, and the leak may well have been what pushed the gang into decommissioning. These logs, and their contents, will be discussed later in this article.
The Conti Ransomware gang have proved to be the most dangerous malware outfit in years, and have targeted IT systems of many sectors around the globe. Their double extortion tactics proved so successful that it’s become the de facto tactic of hackers worldwide.
The FBI, who have done extensive research into Conti ransomware, have described the virus as “the costliest strain of ransomware ever documented.”. The Bureau estimate more than 1000 organizations have been hit by Conti Ransomware, and ransom payout exceed $150 million. The payout number is hard to estimate, as many victims will not admit if they paid the ransom or now.
According to AdvIntel researchers, Yelisey Boguslavskiy and Vitali Kremez, the Conti brand is dead, but the organization itself may not be. Members of the group as still skilled, adept programmers, as well as excellent businessmen when it comes to efficiency.
At present, the FBI have played it cautiously with regards to the status of the Conti Ransomware gang. “As this is an ongoing matter, we do not have any additional information to provide at this time,” the Bureau said.
“They might come up under a new name, which happens from time to time, where they kind of rebrand in order to escape some of the reputation or the law enforcement scrutiny on the group,” said Adam Meyers, SVP of intelligence at Crowdstrike.
Conti stands out amongst others not just for its advanced tech, but for its fearless attack on nations. These attacks have felt justified to them after declaring their ties to Russia.
“It’s still quite baffling to see a ransomware group target a country like this. And to also make threats to other countries,” said Allie Mellen, a Forrester analyst.
“The group was creating new tools as recently as last month,”” Meyers said.
“Conti, or whatever it calls itself now, isn’t going to willingly let that go,” he added.
The Work/Life Balance of Hackers
As mentioned previously, the internal communication logs from Conti were leaked some time ago, and they provide a fascinating insight into how the organization functions.
The leaks, after being sent to media, independent journalists, and cybersecurity researchers, were also disclosed on Twitter. In total, there were more than 60,000 chat messages sent among members of the gang. Its source code, and scores of internal Conti documents. The author of the tweet simply stated “Glory to Ukraine”.
The leaks provide a look into the Conti Ransomware gangs operations that has never quite been seen before in the cybercrime underworld. While there is a misconception around how hackers operate due to TV and Movies. However, the logs instead paint a picture of a sophisticated, fully functional business, along with a hierarchy one would expect in any corporation. Furthermore, the logs showcase the hackers individual personalities, ransomware negotiations, and conversations about evading law enforcement.
“We see the gang progressing. We see the gang living. We see the gang committing crimes and changing over the course of several years,” says Alex Holden. Alex Holden, whose company Hold Security has tracked Conti members for most of the last decade.
The Conti Ransomware gang, like any business, has multiple departments, from HR and administrators, to programmers and researchers. It has best-practice cases for how code is written, and best-practices around how members should evade authorities.
The leader of the gang – effectively, CEO – is named Stern, and often goes by the handle ‘Demon’. To other members of the gang, Stern is known as “big boss”. Every member in the group uses various handles which change often. Stern seems to value accountability and productivity above all else. “Hello, how are you doing, write the results, successes or failures,” Stern wrote in one message sent to more than 50 Conti members in March 2021.
Another top member at Conti is Mango, who seemingly works as a general manager. He frequently goes on tirades to Stern in private chat, either complaining about workers, or giving updates. “They seem to be responsible for procuring different tools for different departments and making sure that the employees are being paid,” says Kimberly Goody. Kimberly Goody is the director of cybercrime analysis at security firm Mandiant.
The team have fluctuated in size. In the middle of 2021, Mango tells stern that the organization consists of 62 people. Later, this grows to 100. They have to seem to have an issue with keeping staff too, as members drop off regularly. Stern wishes to keep the group growing – In one chat log, Stern says they are thinking of recruiting 100 more participants. “The group is so big that there are still middle managers,” group member Revers tells Meatball in June 2021.
Members are recruited via hacking websites as well as legitimate job websites. There is an onboarding process – When a members joins, they’re introduced to their team leader, who will assign their tasks. “I will hold a planning meeting in the evening and appoint you to the team,” Revers says in another message.
“What could be striking at first glance is the size, structure, and hierarchy of the organization,” says Soufiane Tahiri. Soufiane Tahiri is a security researcher who has been reviewing the documents. “They operate pretty much like a software development company. Contrary to popular belief it seems that many coders have salaries and do not take part in the paid ransom.”
The salaries do not reflect the intensity of their work, with many programmers making below $2000 per month. The group even claimed to have an unnamed journalist on its payroll in April 2021, who would get a 5 percent cut by helping put pressure on victims to pay up. “We have salaries on the 1st and 15th, usually 2 times a month,” Mango tells one member of the group.
Money is often discussed in group chats in the gang. The logs show lengthy debates regarding the cost of ransoms that should be charges.
“We found through our logs that they have the full plethora of manuals of how they should maintain team spirit,” says Vitali Kremez. Vitali Kremez is the CEO of security company AdvIntel. Kremez’s research is name-checked by Conti multiple times throughout the chats. “They are not just making money, they are thinking about people. The think how to be more successful in the environment they have created.”
Many of the conversations are standard water-cooler talk – About girlfriends, sports, weekend plans. These are in quite a contrast when considering what the gang actually do for a living.
“There were channels created specifically for potential victims or infected victims,” says Émilio Gonzalez. Émilio Gonzalez is a Canadian security researcher who studied the Conti files and re-created the group’s Rocket. Chat conversations. Companies are listed as “dead” or “done” in channel names. Each channel has two to four participants with different levels of seniority and responsibilities, Gonzalez says. “The conversation usually starts with credentials or access to a specific machine on the network of the victim.” The attacks then progress from there. A review of February 2022 RocketChat messages by The Intercept shows the group discussing drug use content in general channels. Also, making anti-Semitic comments about Ukrainian president Volodymyr Zelensky.
Despite the apparent friendship, there are often plans in the logs to take out other members. One member in particular is discussed quite often, who goes by the handle Dollar.
“Let’s get the dollar out of the game,” Cyberganster wrote to Mango. “He is a fcked up bstard.” It is believed Dollar was using Conti target hospitals, which are not considered fair game in Ransomware culture. Of course, Conti actually broke this rule themselves later. Six days after the complaint from Cybergangster, Mango confronts Dollar. “You really [are] more problems than good,” one message in a series of 11 says. Mango says “everyone constantly complains about you and gets angry” and accuses Dollar of spoiling the gang’s “reputation” by targeting hospitals.
With the release of their these logs, many details were disclosed about Conti and its members. These include a trail of personal details, such as the handles they use online, Bitcoin addresses, and email addresses. “If this information is true, it definitely makes life easier for law enforcement,” says Tahiri. “By dismantling the group behind Conti we can be sure that the whole infrastructure will suffer.” It’s something the group’s members are well aware of: “We are already in the news,” read one of the last messages sent before the leak.
Let’s take a look at some of their biggest attacks of the Conti Ransomware Gang in the last two years.
Conti Ransomware Vs The HSE

In May 2021, the Irish Health service, known as the HSE, was entirely overwhelmed by a Conti Ransomware attack. After the attack, over 80% of its systems were encrypted.
The attack staggered the HSE throughout Ireland, leading to severe distruptions in public and private clinics, as well as every hospital in the country.
The attack itself exposed the information of nearly every citizen who had received a COVID-19 vaccine to date, and the information stolen was nearly 700GB in size. The data stolen was sent directly from the HSE’s network to the attackers’ servers.
Though details concerning the attack were scarce at first, an independent post-incident review revealed the scale of the attack. Notably, the review pointed out that the primary cause of the attack was the lack of the HSE’s preparedness to deal with any sort of cyberattack on its network.
“The HSE did not have a single responsible owner for cybersecurity, at senior executive or management level at the time of the incident. There was no dedicated committee that provided direction and oversight of cybersecurity and the activities required to reduce the HSE’s cyber risk exposure,” the HHS report said.
“The lack of a cybersecurity forum in the HSE hindered the discussion and documentation of granular cyber risks, as well as the abilities to identify and deliver mitigating controls. The HSE did not have a centralized cybersecurity function that managed cybersecurity risk and controls.”
To add to all of this, the HSE had absolutely no security monitoring solutions deployed across its IT environments which would help in monitoring and remedying attacks across its network.
Due to this, Conti Ransomware was given free run of the health service network. The review revealed several Cobalt Strike beacons being deployed across servers weeks before the attack. These beacons were detected by endpoint antivirus solutions, but the alerts were ignored.
“The impact of the ransomware on the IT environment was reported by the HSE’s management to lead to 80% encryption,” the report added.
“The impact of the ransomware attack on communications was severe, as the HSE almost exclusively used on-premise email systems (including Exchange) that were encrypted, and therefore unavailable, during the attack.”
Eventually, the Conti Ransomware gang gave the health service a free decryptor to at least make systems operational again. However, there was an added caveat – The data would be sold and/or published if the HSE did not pay a $20 million ransom.
“We are providing the decryption tool for your network for free. But you should understand that we will sell or publish a lot of private data if you will not connect us and try to resolve the situation,” the Conti ransomware gang said on the negotiation chat page.
“The HSE is aware that an encryption key have been provided,” the Irish Department of Health told BleepingComputer at the time. “However further investigations have to be conducted to assess if it will work safely, prior to attempting to use it on HSE systems.”
The attack lead to intense coverage nationally and internationally. The Taoiseach of Ireland, or Prime Minister, stated that the ransom would not be paid.
The information was eventually leaked. To this day, there is not much known about who bought the data, or where on the dark web it is being kept. Usually, in cases like these, information such as medical records are used in identity theft – and these cases can take years to manifest the full extent of damage.
Conti Ransomware Takes Aim On Tulsa

May 2021 was indeed a busy month for the Conti Ransomware gang, as shortly before the attack on the Irish health service, they carried out a devastating attack against Tulsa, Oklahoma. The city is the second largest in the state, and home to over a million residents.
The gang attacked a number of government organizations within the city, including both the water systems and police service. The water systems were brought entirely offline, and websites for every city organization was taken down.
From the police service, the Conti Ransomware gang stole the records of 18,938 people, as well as internal documents. Much of the data was compromised of police citations. Shortly after the attack, the police service issued a statement to citizens to be on the look out for evidence of identity theft within their personal accounts.
Though the citations did not include social security numbers, it did include information such as name, date of birth, address and driver’s license number – all valuable currency on the dark web.
“Out of an abundance of caution, anyone who has filed a police report, received a police citation, made a payment with the City, or interacted with the City in any way where PII was shared, whether online, in-person or on paper, prior to May 2021, is being asked to take monitoring precautions,” according to the statement.
Though SSNs are usually the silver bullet when it comes to pulling off identity theft successfully, the other information can be used in social engineering and phishing attacks by hackers to garnish further information.
“In this instance, the disclosure of police records can be used to construct convincing stories to trick unsuspecting victims or their families into paying fake fees or fines by claiming to be lawyers or court representatives,” Chris Clements, vice president of solutions architecture for Cerberus Sentinel, said in an email to reporters. “Even normally scam-savvy people may be fooled if a fraudster has enough detailed information.”
The attack was said by many to be the Conti Ransomware Gang simply showing off its power – To them, nobody was safe.
“The Conti group is showing a blatant disregard for the authority of law enforcement as they continue their attacks on these vital services,” Erich Kron, security awareness advocate for KnowBe4, said in an email to reporters. “Even after the shutdown of the DarkSide gang, the arrests in the takedown of the Clop group, and even in light of the Ziggy ransomware gang providing all of their encryption keys for victims due to the fear of law enforcement actions, Conti continues their attacks without skipping a beat.”
The Conti Ransomware Gangs Biggest Corporate Heist
In one of their biggest corporate attacks, the Conti Ransomware gang stole 1.7TB of data from Japanese company JVCKenwood, and demanded a $7 million ransom. JVCKenwood are an international brand with billions of dollars in revenue each each. They’re known for their brands JVC, Kenwood, and Victor, which manufacture car and home audio equipment, healthcare and radio equipment, professional and in-vehicle cameras, and portable power stations.
The attack took place in September 2021, and knowledge of the attack was brought to light by JVCKenwood when they disclosed that its sales companies in Europe were breached.
“JVCKENWOOD detected unauthorized access on September 22, 2021 to the servers operated by some of the JVCKENWOOD Group’s sales companies in Europe. It was found that there was a possibility of information leak by the third party who made the unauthorized access,” JVCKenwood announced in a press statement.
“Currently, a detailed investigation is being conducted by the specialized agency outside the company in collaboration with the relevant authorities. No customer data leak has been confirmed at this time. The details will be announced on the company website as soon as they become available.”
Sources who got hold of the ransom note at the time confirmed that it was the Conti Ransomware gang.
In the negotiation chat, the gang demanded a $7 million ransom not to publish the 1.5TB of data and to provide a decryptor.
Despite the company claiming the attack was not as bad as it seemed, hackers in the Conti gang shared a PDF file showing scanned passports for JVCKenwood employees, a sign that there was plenty more sensitive data on their servers.
To date, JVCKenwood have never released on a statement regarding if they paid the ransom or note. Many commentators and researchers do believe they did eventually, however.
Costa Rica In A State Of Emergency

Proving that there is no target too big, the Conti Ransomware gang caused the Costa Rican President Rodrigo Chaves to declare a national emergency following an assault by the group a number of government entities.
The attack occurred in May just gone, and Conti have already published a large portion of the 672GB stolen from the Costa Rican government.
The emergency was signed into law on May 8th, which was the same day Chaves assumed office as the country’s 29th president.
Costa Rica’s Social Security Fund (CCSS) had previously stated, “a perimeter security review is being carried out on the Conti Ransomware, to verify and prevent possible attacks at the CCSS level.”
According to cybersecurity researchers, Conti’s data leak site had been updated to state that the group had leaked 97% of the 672GB stolen.
The first government entity to feel the attack was the Ministry of Finance, which still hasn’t evaluated the full extend of the attack on taxpayers’ information, payments, and customs systems
Before the leak, the Conti Ransomware gang had demanded a $10 million ransom, which was not paid.
The leak seaked published information on the following agencies:
- The Costa Rican Finance Minsitry, Ministerio de Hacienda
- The Ministry of Labor and Social Security, MTSS
- The Social Development and Family Allowances Fund, FODESAF
- The Interuniversity Headquarters of Alajuela, SIUA
It is also believe SQL data from government websites was published.
Instead of attributing the attack to being state-sponsored hackers, Conti claim to have acted of their own volition. At the time, the gang promised future attacks would continue at this level of severity.
“The attack that Costa Rica is suffering from cybercriminals, cyberterrorists is declared a national emergency and we are signing this decree, precisely, to declare a state of national emergency in the entire public sector of the Costa Rican State and allow our society to respond to these attacks as criminal acts,” said the President, accompanied by Minister of the Presidency, Natalia Díaz, and the Minister of Science, Innovation, Technology and Telecommunications (Micitt), Carlos Alvarado.
“We signed the decree so that the country can defend itself from the criminal attack that cybercriminals are making us. That is an attack on the Homeland and we signed the decree to have a better way of defending ourselves,” added President Chaves.
Other agencies hit by Conti within the country are:
- Administrative Board of the Electrical Service of the province of Cartago (Jasec)
- The Ministry of Science, Innovation, Technology, and Telecommunications
- National Meteorological Institute (IMN)
- Radiographic Costarricense (Racsa)
- Costa Rican Social Security Fund (CCSS).
Conti’s Busiest Month
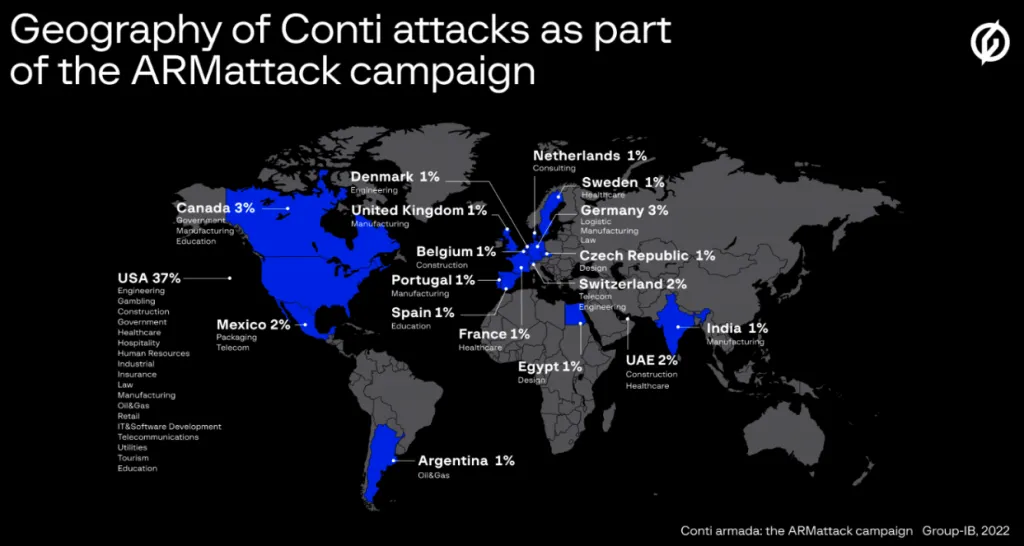
As you have read, the Conti Ransomware gang is an aggressive cybercrime outfit which is extremely organized. However, one month stood out for them more than any – Between November and December 2021, when they managed to hack over 40 separate companies from locations all over the world.
The month-long campaign, known as ARMattack, has been described by cybersecurity researchers as being one of the group’s “most productive” and “extremely effective.”
Group-IB, an organization who have spent the most time researching Conti, detailed ARMattack some months ago, and gave it its name – based off the domain the gang were using at the time.
During ARMattack, Conti managed to breach more than 40 organizations across various sectors. While there was clearly a focus on American companies, nearly every continent was affected in the campaign.
A Group-IB spokesperson told reporters that ARMattack was very swift and explained that the company’s report refers to organizations that had their networks compromised. It is unknown whether any of the victims paid the ransom demanded by the attacker.
It is worth noting that while the Conti leak site published data for as many as 46 victims in just one month (e.g. April 2022), the compromise date remains unclear.
“After gaining access to a company’s infrastructure, the threat actors exfiltrate specific documents (most often to determine what organization they are dealing with) and look for files containing passwords (both plaintext and encrypted). Lastly, after acquiring all the necessary privileges and gaining access to all the devices they are interested in, the hackers deploy ransomware to all the devices and run it” said the Group-IB spokesperson.
Group-IB, who have had insight into Conti’s internal chats, even went as far as to analyze the working hours of Conti members and programmers. They concluded that the average Conti member worked 14 hours every day, only take a New Year holiday. This sort of work schedule accounts quite a bit for their efficiency.
“Conti’s increased activity and the data leak suggest that ransomware is no longer a game between average malware developers, but an illicit RaaS industry that gives jobs to thousands of cybercriminals worldwide with various specializations” – Ivan Pisarev, Head of Dynamic Malware Analysis Team at Group-IB’s Threat Intelligence team
Conti Ransomware Analysis

In breaching any network, the gang will use a number of tactics.
This may first begin with social engineering, and trying to convince employees to hand over credentials. In more difficult cases, members can attempt to exploit vulnerabilities, or or attack the internet-facing RDP (Remote Desktop Protocol) servers.
Once a gang member has breached the network, they will usually attempt to gain access to the domain administrator account.
If the hacker does gain this access, they will be able to deploy Conti ransomware on the network. At this moment, the attacker might also gain access to accounts with extra priviledge, in order to steal important information, including backups. When they are at this level, they can also tinker with security settings to avoid being noticed. This allows them to move laterally across the network while their presence is obscured.
Before the attack, the gang will usually scan the network for servers, endpoints, backups, sensitive data, apps, and protection software. IP addresses will also be compiled, as well a list of server names.
Popular post-exploitation tools like Mimikatz, which dumps credentials from memory, are frequently used by attackers. They could also try to break things on purpose in order to grab the administrator’s credentials when they login to examine the problem.
Commonly, backdoors are also installed, to allow for future attacks. These backdoors also allows the gang to transfer data to their Command & Control (C&C) servers and monitor network traffic. This is beneficial in knowing how the victim is recovering from the attack. They’ll frequently utilize programs like AnyDesk and Cobalt Strike to help them with remote access and control, as well as Tor proxies to hide their contact with the C&C server.
Before the ransomware is executed, the gang will try to steal as much business-critical data as possible. Data discovery technologies are frequently used by attackers to identify sensitive data. This data can be saved on their owner server, or uploaded through anonymous cloud storage.
Once all information has been lifted, backups have been deleted, and security measures have been disengaged, the attackers will execute the ransomware. Batch scripts are used to loop over identified IP address to deploy Conti to as many servers and endpoints as possible. In advanced cases, they infect a logon script in a Group Policy Object (GPO), which runs the code every time the computer starts up and joins the domain.
Once encryption is complete, and note is dropped on the users systems, stating the terms of ransom and how it is to be paid. In the majority of cases, the user is powerless when it has reached this stage.
The Future Of The Gang
It is difficult to say for sure if Conti are to be believed, and that the organizations has shut down. As Meyer puts it, “It’s all kind of a ‘no honor amongst thieves’ type of situation where you can believe what they say, but still take it with a grain of salt.”
Shier has a similar sentiment, “These are criminals who wouldn’t think twice about lying and cheating to make a buck”
It is possible that Conti are merely regrouping for a more high-level attack campaign, which they initially threatened in previous months. However, researchers note that at the end of the day, its the ransom money they’re after.
“For any organized business, cybercriminal or not, the bottom line is very often always more important than political positioning,” one researcher said.
The U.S. government and others need to take these threats seriously and prepare adequately because cyberattacks on government institutions or political leaders can have geopolitical ramifications, according to Mellen.
At what point, she asked, does a cybercriminal outright targeting government officials and infrastructure become a combatant?
Meyers maintains Conti’s mandate is to make money, he said. “They’re a significantly large organization, they’ve got a lot of mouths to feed. And as long as there’s money to be made doing these types of data extortion and ransomware operations, they’re not going to shut down.”
To other researchers, there is a belief that the gang have become several splinter cells, all striving to start their own operation. This could potentially be more harmful than one singular gang.
Or perhaps, Conti really is gone, in all forms. It’s unlikely, but such things have happened. Only time will tell.
How To Protect Against Threats Like Conti
No matter if Conti is truly gone or not, ransomware will remain a fact of life for all internet users, be they individuals or businesses. There are several steps you can take to protect yourself or your business online.
Firstly, attempt to foster a cybersecurity aware culture or mindset. The best defense is a good education, and keeping your wits about you. Phishing and social engineering are the most common routes into a network, and need to be taken seriously. Strange e-mails or websites are the door to a full network infection. Take note of grammar, mistakes, or potential impersonations. Treat every click on an email as a serious issue and potential threat to your entire network. Security Awareness Training as well as phishing simulations for employees can go a long way in educating a group to the dangers of cybercrime.
Secondly, keep software patched and up-to-date. This can seem trivial, but vulnerability exploits are a key attack vector for hackers, and unpatched software can lead to harsh infections. Security researchers work tirelessly on updating software to iron out any vulnerabilities, so take heed of any updates offered.
Thirdly, for networks with many users, apply the principle of least privilege (POLP), a zero-trust theory. Users should be granted the minimum amount of access to applications and systems to perform their tasks, no more and no less. In case of a breach, a segmented series of access like this can shut down attackers right away and lets security teams know that they’ve become a target.
Additionally, make and maintain backups of your network and critical systems. As you’ve read, advanced ransomware strains such as Conti can take these backups offline, but this hasn’t always been the case, and sometimes the likes of Conti can fail to locate backups. This effectively neutralizes an attack – The business may lose a day or two of work, but the alternative is much worse.
Lastly, but by no means least importantly, is using a multi-layered cybersecurity approach. Reliable cybersecurity solutions to safeguard your network are essential, even with the rest of the recommendations above checked off. There are an endless amount of tools such as firewalls, file-scanner, automated software patching, but one of the best solutions you can choose is SaferNet. SaferNet is an always-on VPN designed with cybersecurity in mind. While other VPNs are more geared toward location-spoofing and the like, SaferNet was built to work as a cybersecurity solution for individuals as well as businesses of any size. Furthermore, SaferNet was designed to protect against many attack vectors associated with ransomware, such as phishing attacks. It truly is an all-round solution for all cybersecurity needs.. The
SaferNet – The Solution To Ransomware
Attacks like the Conti Ransomware campaign show that cyberattacks are increasing at an exponential rate, and both government and business leaders are underprepared to face the fallout of an attack. There are several tools internet users should use to increase their online protection. One of these tools is SaferNet.
SaferNet is the perfect solution to the cybersecurity issues that individuals, families, and businesses face today. It not only connects every device using a secure, 24/7 always on, military grade VPN, but it also stops outside cyberthreats, malware and viruses as well. On SaferNet, all users are protected anywhere in the world, all the time, on any cellular or Wi-Fi network. In addition to SaferNet’s VPN and cyber protection, it also offers a range of employee or parental/family internet controls including internet filtering, monitoring, scheduling, and blocking access to websites or even entire website categories
Typically, a business or family would need 3 separate services for a VPN, Malware Protection, and Internet Controls; SaferNet offers all 3 features in one service. SaferNet truly is an endpoint security presence that can be implemented in minutes around the world, on phones, laptops, tablets, and computers at an economical price point that caters to all sizes of businesses and families. SaferNet guarantees a smooth setup and installation process that takes only minutes, and an easily accessible control hub for you to monitor all your employee’s or family members devices; including activity, time spent online, and threats blocked.
The post The Conti Ransomware Gang: A Retrospective first appeared on SaferNet VPN.



